How to Build and Parse JWTs in Java with JJWT
Video/Stream
This screencast walks you through creating JWTs with the Java library JJWT.
Video/Stream
This screencast walks you through creating JWTs with the Java library JJWT.
Tutorial: How to build a Maven plugin.
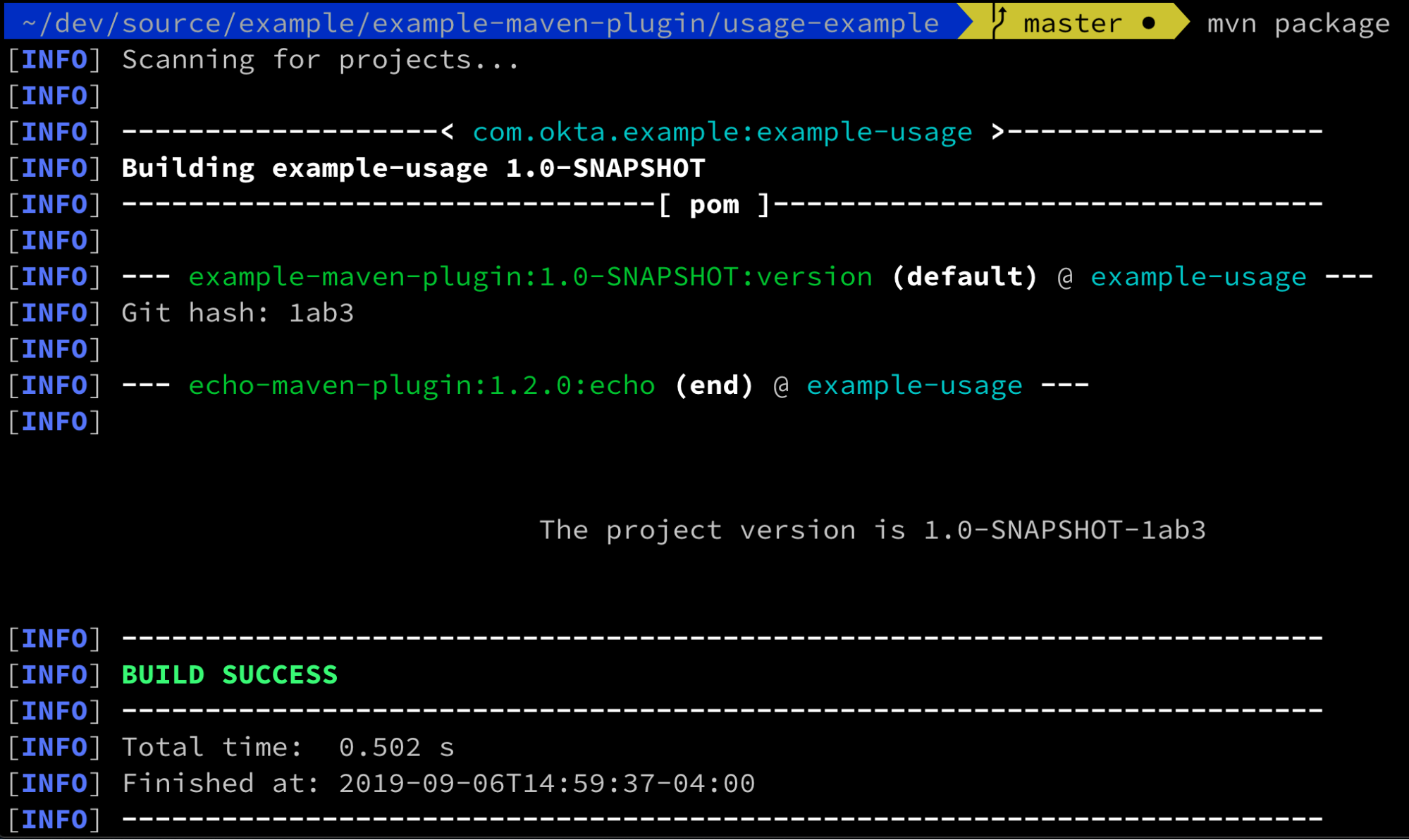
Apache Maven is still the most popular build tool in the Java space, thanks to the popularity of its ecosystem of plugins. It’s easy to find an existing plugin to do almost anything your application needs, from ensuring your source files have license headers, to validating binary compatibility between versions. Occasionally though, you need to write a custom plugin to fulfill a requirement in your product.
A tutorial on testing Java code with Groovy.

My favorite way to test Java code is with Groovy. Specifically, writing tests in Groovy with Hamcrest. In this post, I’ll walk through how to test a simple Spring Boot application with these tools.
Groovy is an optionally typed dynamic language for the JVM, and can be compiled statically. That is a mouthful and I’ll explain this as we go, but for now think of Groovy as Java with lots of sugar.

I’m excited to announce that I’ve joined Okta’s Developer Relations team! I’ve been working on Okta’s awesome Developer Experience team for the last couple years so I’m not exactly a new face around here. 😉

Most OAuth 2.0 guides are focused around the context of a user, i.e., login to an application using Google, Github, Okta, etc., then do something on behalf of that user. While useful, these guides ignore server-to-server communication where there is no user and you only have one service connecting to another one.